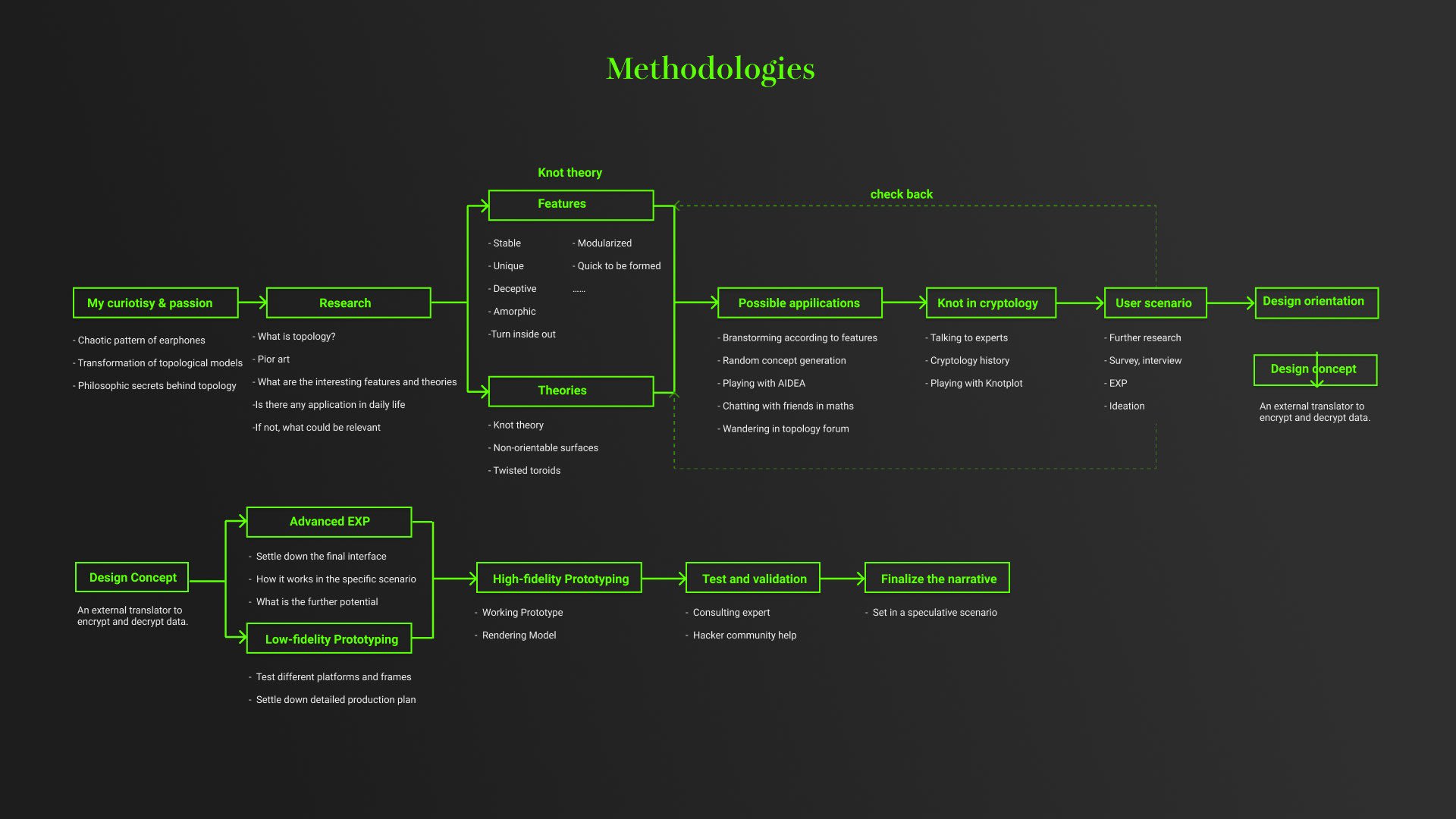
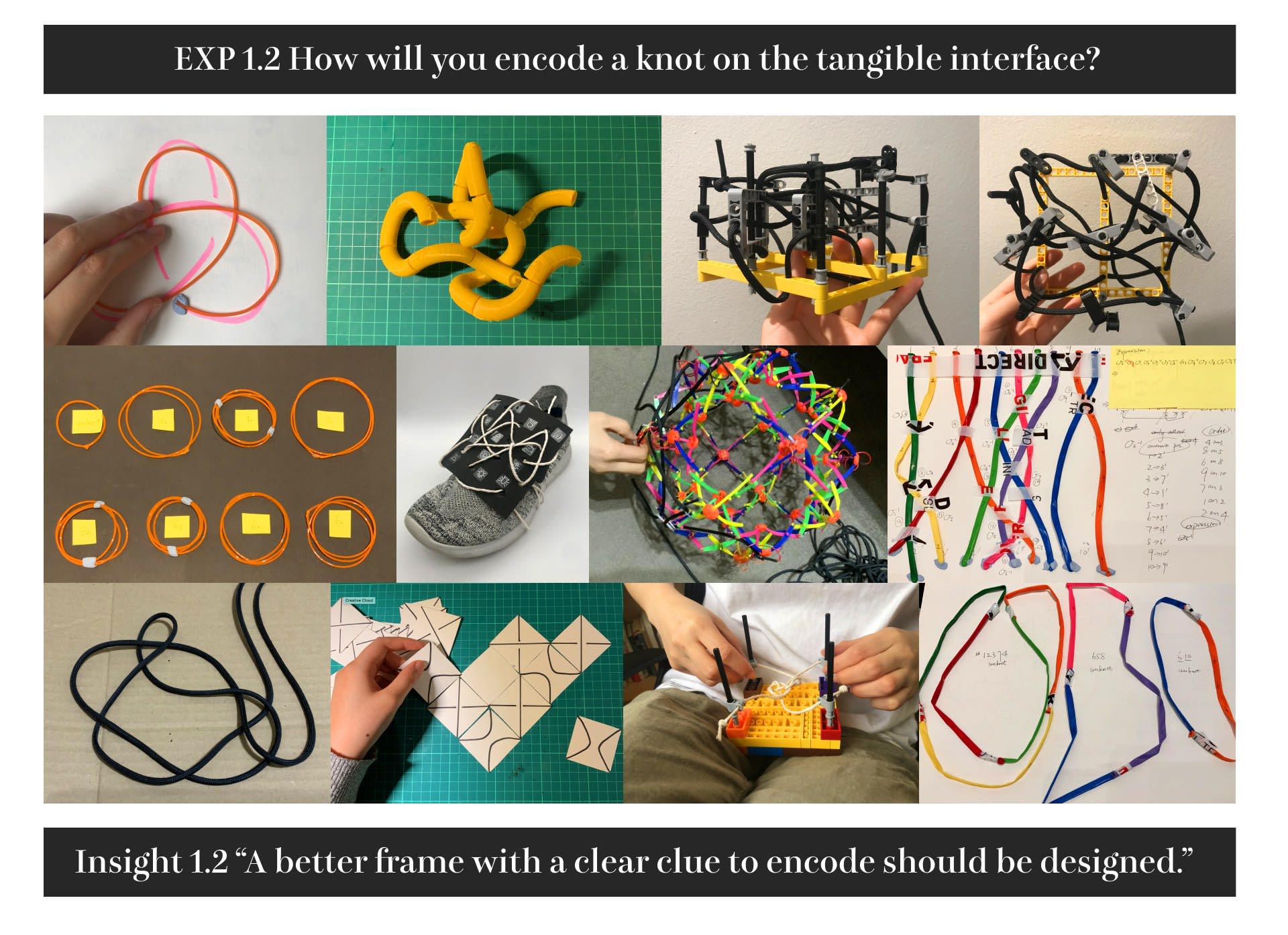
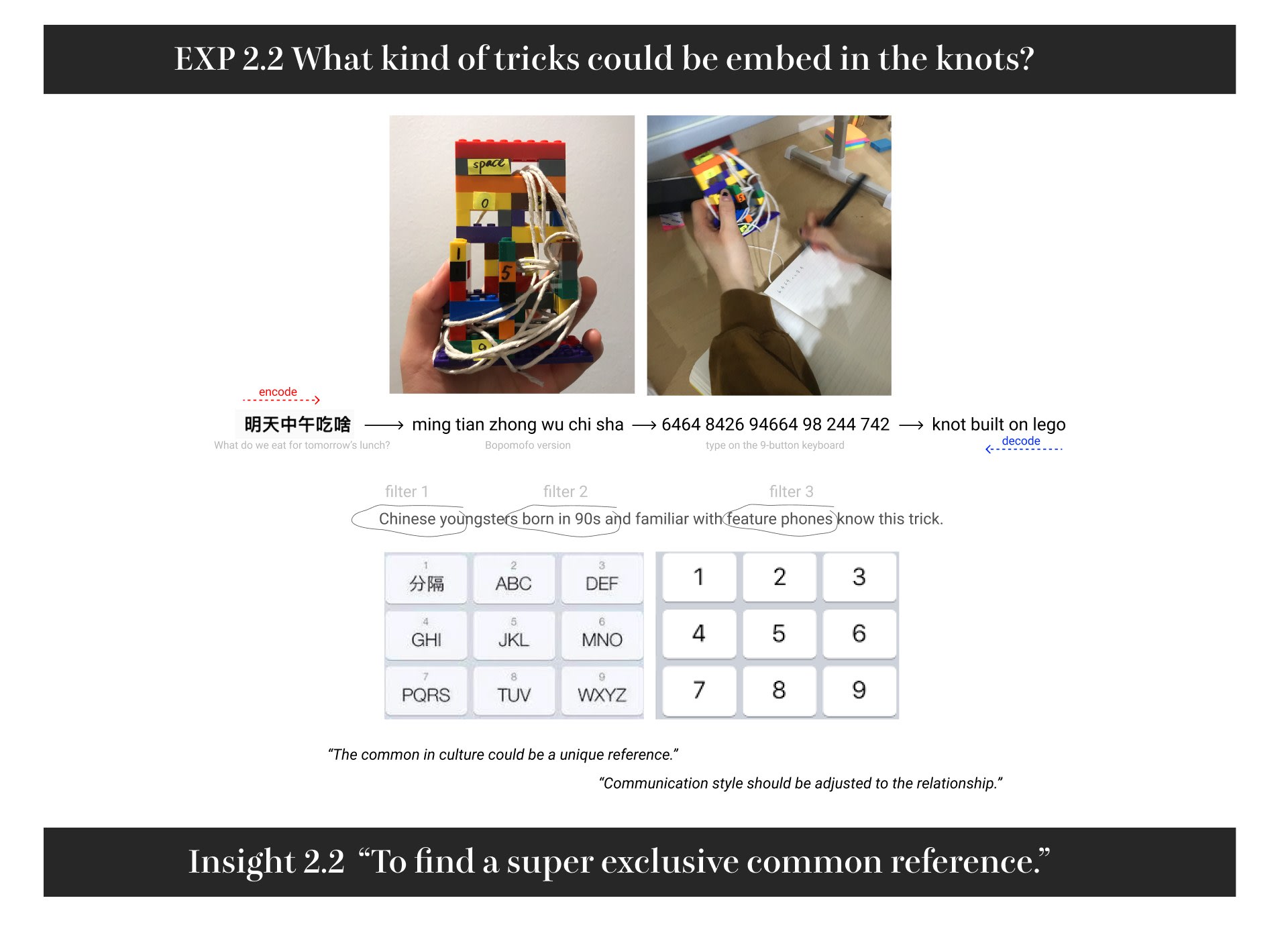
Hello there! I am Danyi Shen (Zoey) :
An Innovation Design Engineering graduate student at Imperial College London (@ ICL) and Royal College of Art (@RCA).
A product designer who has a multidisciplinary background and has worked for designaffairs GmbH and TG0 LTD.
A creative technologist who has a keen interest in embedding daily humour into serious technical implementation.
A start-up co-founder who is developing an AI-led ideation tool to better incubate ideas for designers.
Feel free to contact me even you just want to have a chat.